Hello, I was eagerly waiting to share this with you! 🙂 Due to the two reasons.
- It’s Account Takeover
- And I wanted to tell you, “How Important is to revisit your old target to pwn the new features!”
I have already shared one of the write-up on Privilege Escalation on Facebook’s product! If you haven’t read that yet you can check here.
There are always questions in every newcomer’s mind, “This program is old. All great hackers have already participated, how can I get a bug in this product”?
The answer is, “There are new features that are added to the product regularly and can be missed by anyone or other hackers might be busy with other programs”!
To be honest, it should be an encouraging fact that, “you are able to hack successfully even that was tested previously by some great experts!” It is just a game of perspective! 🙂
You should consider signing up for a newsletter for your target!
THE BUG:
This Program is one of my favorites for a long time. I had a great run with it! I received details in an email of newly added features on my target’s product and I have decided to check and try my skills to pwn those features!
While testing I have noticed one of the endpoints is disclosing “Password reset token, Salt, Invitation token” which every hacker would love to have.” But what makes it more interesting is, that endpoint is only meant to be available for an admin user. When I found that endpoint I was an admin user and obviously, I wanted to achieve more impact. To do so I logged in with my lower Privileged user and hit the same API With the GET request.
The Following Image shows a lower Privileged user gets the password reset token of an admin user.
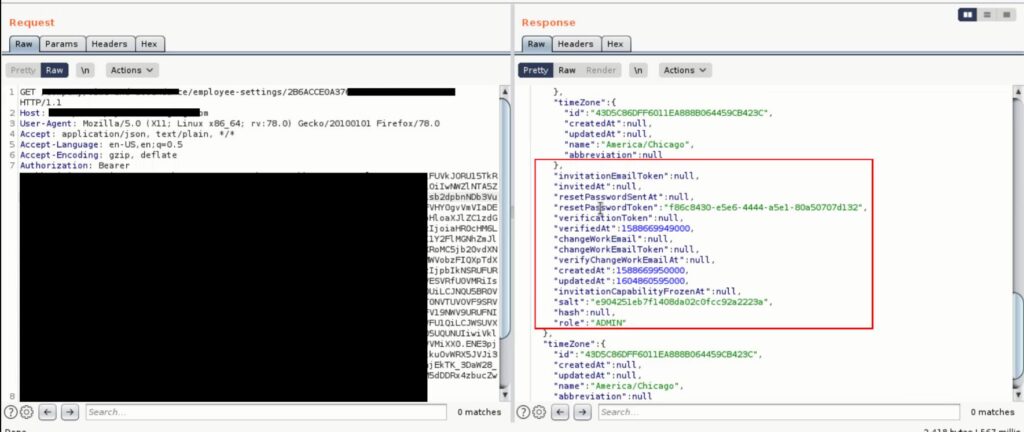
A user ID is an “MD5” hash that is accessible to everyone from the “employees” section. As you can see in the above image some juicy information is leaked by the application server.
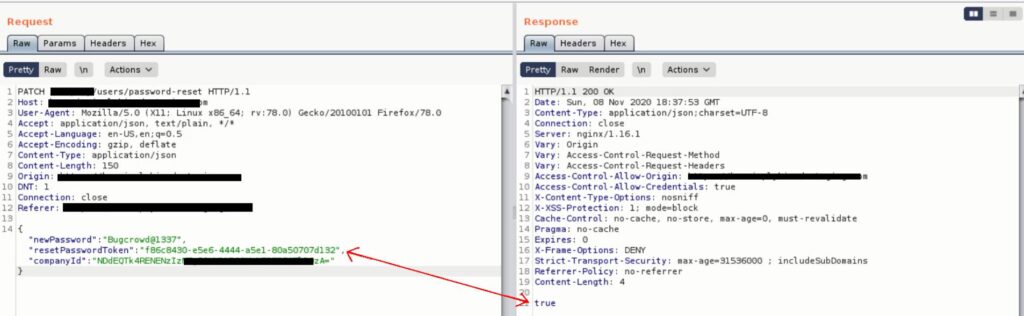
The Next step was to use that Reset Token to change the admin password and take over the admin account!
I went to forgot password page and I have requested a token for my lower privileged user(attacker)! After receiving the password reset link I captured the request and changed the token and submitted a new admin password. The request was successful and I was able to take over the admin account! As a matter of the fact, I was able to take over any account of the same organization! It could have been a disaster if a cross-organization account takeover was possible.
The following image shows the successful request for an admin account takeover!
I was able to find this bug just because I have subscribed to their newsletter! As soon as I confirmed the issue I notified the team.

Timeline to remember:
- — Bug Reported
— Bug Triaged
— Bug Patched
Impact:
The bug could allow any lower privileged user to takeover admin and/or any other normal user account!
This is one of the techniques to take over the account! Want to learn more other ways? Click here to check out these slides on account takeovers. Also, don’t forget to check out our workbook.
What’s next?
I might share more write-ups but one interesting topic on knoxss is definitely coming in near future!